| Overview
Tcpdump prints out the headers of packets on a network interface that match the boolean
expression. The modified tcpdump can print Netloggerized tcp message for a specified host
and port. The original functions of Tcpdump-3.4 stay the same.
Platform
This modified tcpdump is modified from Tcpdump-3.4 for linux. Using libpcap-0.4. It is
tested on RHT 6.0, Kernel 2.2.13-KURT on an i686.
Install
The modified tcpdump is tar and gzip to netlogger_tcpdump.gz. Please gunzip and tar the
file before installation. The installation is the same as Tcpdump-3.4.
Readme
- To Start Netloggerized tcpdump, add -A option in command line. If you don't add -A
option, the tcpdump will act as before modified. If you will listen only tcp message,
please add 'tcp' in command line.
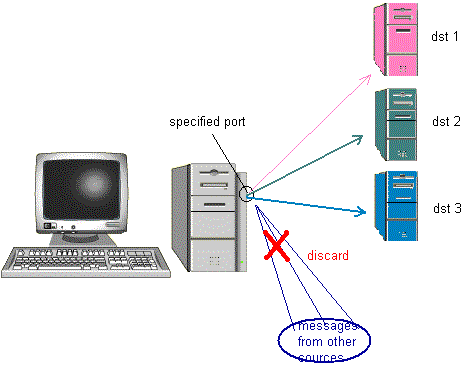
- Netloggerized Tcpdump can monitor the specified host and port. If
you want to monitor the local host, please list the local host name in command. If
only the host is specified, the modified tcpdump will monitor all the ports on this host.
If host name and port are all specified, the modified tcpdump only monitor the messages
from the port. The messages which the source host and port are specified are monitored,
other messages are discarded.
eg. tcpdump -A tcp and host testbed10.ittc.ku.edu and port 22
- The messages which are retransmitted or window changes, will be output in two ways, to
screen or to a file. If you want to write the messages to a file, please add -w option,
otherwise the messages are printed to screen. The file can be viewed using vi, pico or
other editors.Using Netlogger C API to write to a file.
eg. tcpdump -A tcp and host piggy.ittc.ku.edu and port 21 (print to screen)
tcpdump -A -w piggy tcp and host pigy.ittc.ku.edu and port 21 (write to a file named
piggy)
- The format of the message is as below
DATE=20000408201807.491352 HOST=testbed10.ittc.ku.edu PROG=tcpdump
LVL=Error NL.EVNT=TCPD_REXSEG SN=1098 SRC_HOST=testbed10.ittc.ku.edu
SRC_PORT=22 DST_HOST=kermit.ittc.ku.edu DST_PORT=1825
DATE: UTC time of this packet received
HOST: local hostname
PROG: "tcpdump"
LVL: According to the definition in head of the file logging.c(from
Netlogger C API),if the message is retransmitted, LVL is "Error". If the
message's window size changes, LVL is "Usage". If the message is both
retransmitted and window size change, LVL is "Error".
TCPD_REXSEG SN: If this message is retransmitted. SN is seq. no. of
this message.
TCPD_WIN CHG: If this message's window size is changed. CHG is the size
of window change.
SRC_HOST: The source host of this message
SRC_PORT: The source port of this message
DST_HOST: The dst host of this message
DST_PORT: The dst port of this message
Changed files
+ Netl_print_tcp.c
+ logging.c // Netlogger API
+ logging.h // Netlogger API
tcpdump.c
print-ether.c
print-ip.c
print-null.c
print-fddi.c
print-atm.c
print-ppp.c
print-sl.c
util.c
interface.h
Makefile
Makefile.in
NOTE
- The messages from the same port maybe have diff. dst. host and dst port. For this
Modified Tcpdump, the massages have the same source can have as many as 100 diff. dst. If
the dst. are above 100, there will has problem.
- The rule for judging the messages whose window size change is as the example below.
SEQ is the seq. no of message and WIN is the window size. From this result, we can see
when the third message comes, the window size changed to 32080 , and the window size
changed back to 32120 with the fourth message. All the third and the fourth messages are
regarded as window size changes.
>SEQ=1 WIN= 32120
>SEQ=2 WIN= 32120
>SEQ=3 WIN= 32080 *
>SEQ=4 WIN= 32120
>SEQ=5 WIN= 32120
>SEQ=6 WIN= 32120
>SEQ=7 WIN= 32120
>SEQ=8 WIN= 32120
|

